Threat Predict
OVERVIEW
A Use Case for Cyber Data Science
Federal Agencies and Security Operations Centers (SOC) are facing a variety of challenges. With a finite number of resources and an increasing number of security threats, cyber teams are striving to drive efficiency and effectiveness. Through discussion and feedback from Federal Agencies, there are several concerns:
- Log volume is overwhelming SOC analysts
- The SOC Monitoring Team experiences constraints in log data identification if Threat Intel, Cyber Hunt, and/or Vulnerability Management Teams have not identified an event and created an alert/playbook for SOC teams to act upon
- With the variation and volume of logs and events, security teams face the difficult task of understanding what “Normal” looks like
- SOC Analysts currently have the ability to see and respond to the last known Tactics, Techniques, and Procedures (TTP), and response occurs with limited resources and abilities to detect a new TTP. The ability to identify and prevent future threats demands new capabilities and resources
- While the vision exists, the data-driven approach to inform and design a Zero Trust Architecture (ZTA) for agencies demands further conversation and introduction of tools and skills to achieve this architecture
These challenges drove the design of the SkyePoint/TIBCO Threat Predict cybersecurity solution to meet these obstacles head on.
WHAT SKYEPOINT AND TIBCO BRING
SkyePoint is a trusted partner across the Federal Government providing tailored solutions leveraging a highly cleared cybersecurity workforce. Our ability to successfully execute unique customer requirements, and demonstrated experience securing Federal Information Technology, including legacy systems, make us the Focused, Innovative, and Trusted partner to our customers. SkyePoint is proud of its track record of operational and technical excellence and is committed to delivering technical and programmatic excellence to ensure customer mission and business success.
TIBCO Software, Inc, (TIBCO) unlocks the potential of real-time data for making faster, smarter decisions. Our Connected Intelligence platform seamlessly connects any application or data source, intelligently unifies data for greater access, trust, and control; and confidently predicts outcomes in real-time and at scale. Our unified platform for Federal partners, is enterprise-class and backed by more than 40 years of combined company experience solving complex challenges and building groundbreaking applications. We believe data and analytics are the drivers of Federal and DOD digital transformation, and we are on a mission to help agencies capitalize on opportunities in the new connected world.
HOW DOES THREAT PREDICT WORK
TIBCO uses security data collected by log management resources and ingests it into the TIBCO visualization tool. Initial visualizations provide context to the agency’s environment. Other data sources are then combined for predictive/prescriptive analysis and anomaly detection: asset management, user data, VPN access requirements, Single Sign-On, end-point security, etc., With the data integrated, data science models are applied and baseline behaviors are established, providing immediate insight into what “normal” looks like on the network (when are systems accessed, by whom, with what frequency, and by what methodology). The machine learning algorithms then automatically look for outliers and patterns within the data that are considered outside of the baseline (I.P. switching, lateral login attempts, increased activity during odd hours, concurrent successful logins, anomalous user tendencies., etc.). Alerts are then delivered to SOC analysts, threat hunters, and other cyber professionals inside a single portal, providing a common operating picture to all levels of cyber personnel.
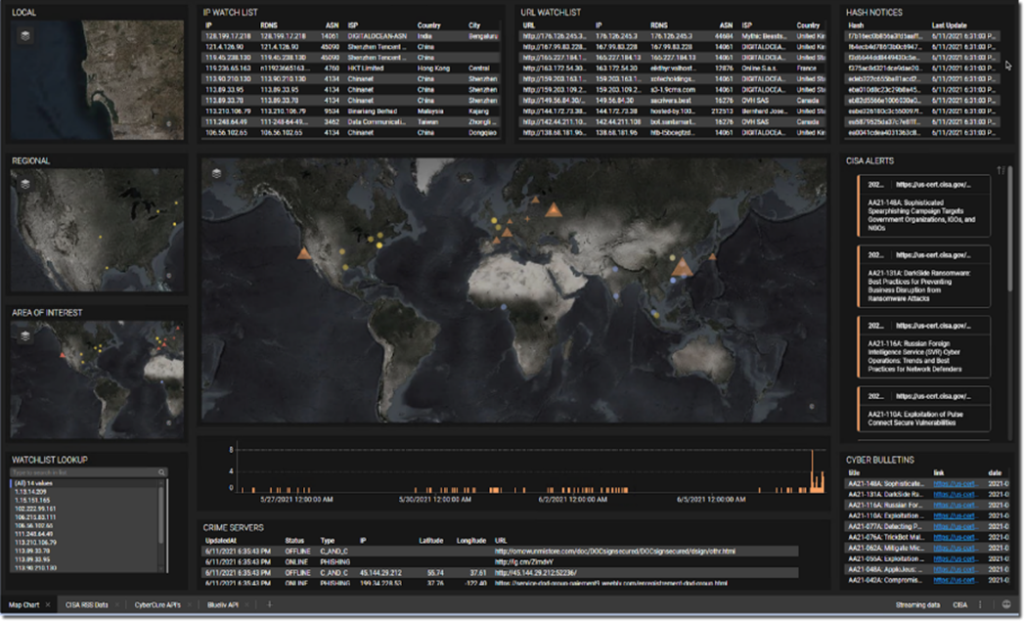
Applying TIBCO ML/AI technology to internal systems combined with TIBCO’s Open Source Intelligence (OSI) Situational Awareness solution, allows for SOC analysts and threat hunters to immediately deconflict sourced anomalies against OSI in a single portal. A positive OSI hit from a ML/AI sourced anomaly can be immediately investigated, providing cyber personnel with proactive rather than receive capability.
TIBCO is currently using this solution with the U.S. Navy to examine known and unknown objects to determine from the unknowns what could be a known entity; and then providing predictive analysis of projected movement of both the known and unknown objects. The patterns of anomaly present like threat actors moving through a network.
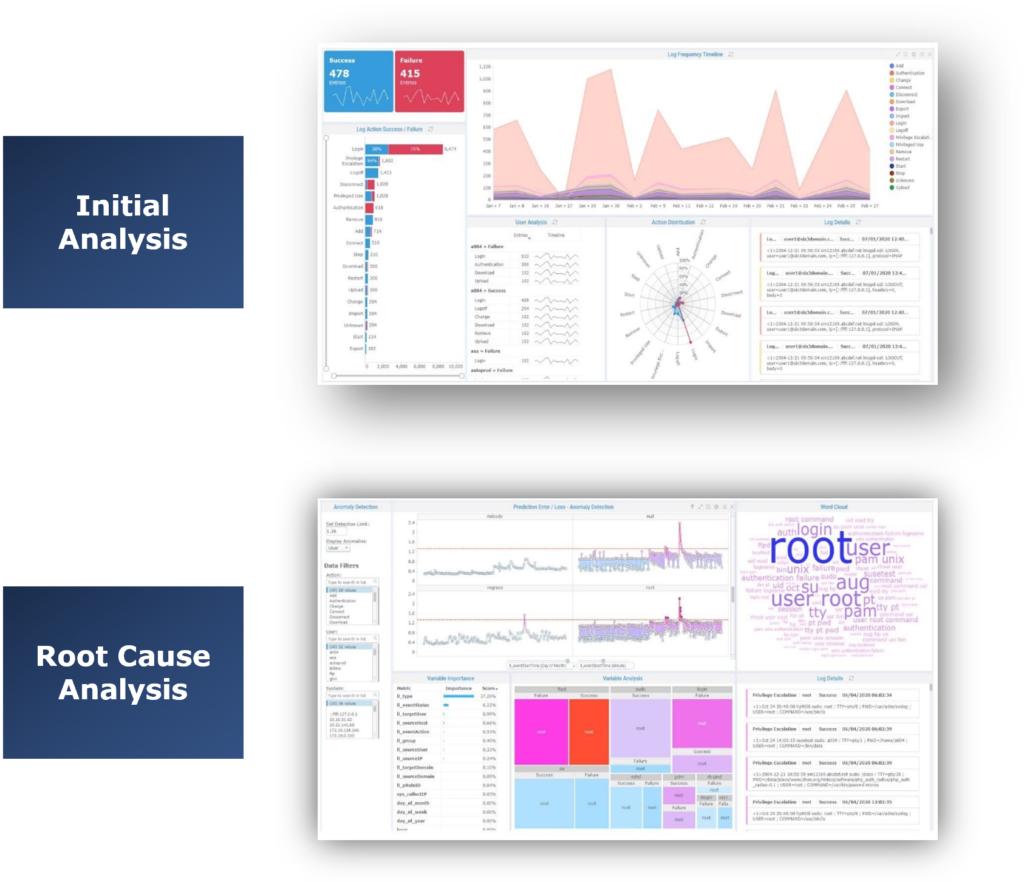
HOW TIBCO DOES IT
TIBCO Spotfire’s robust AI/ML visual analytics tool has technology that spans all the way from predictive models to dynamic visual dashboards, making it the top choice for developing AI applications. Spotfire enables data visualizations of any data, from streaming data to data at rest. The solution’s predictive capabilities are extensible and provide seamless integration with R, Python, SAS, and MATLAB. Advanced, intelligent data integration and visualizations, combined with proven AI and ML technology makes it possible to gain timely, actionable insights without knowing where to look through alerting to the anomalous patterns, trends and outliers on your network; empowering SOC personnel while informing on Zero Trust architecture policy.
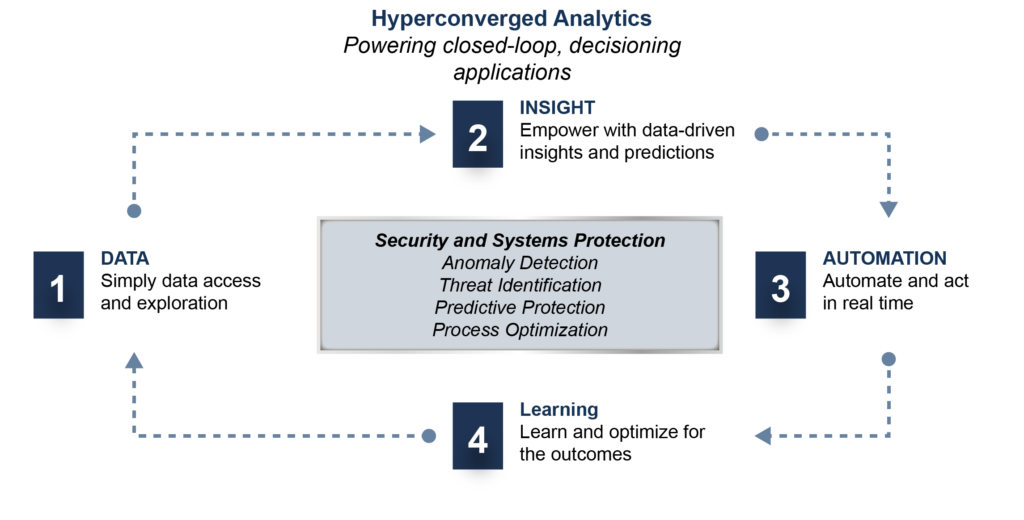
SOLUTION FEATURES



LEARN MORE

Find out how SkyePoint can help you manage and operate your IT mission environments more efficiently.