

Do you need to Utilize
a Threat Defense Shield®?

SkyePoint is a leading cybersecurity, IT engineering, software,
and secure mobility small business integrator.
Turn Your Ideas into Actions

SkyePoint Solutions
Provided for clients who are looking for:
- Integrated Cybersecurity operations providing continuous monitoring of controls while identifying and rapidly responding to cyber incidents and actionable threats.
- NIST RMF approach that reduce the threat surface and achieve FISMA compliance.
- Security Architecture and Engineering capabilities that provide “right sized” Security Controls.
SkyePoint is an ISO 9001:2015 and ISO 27000 certified company.

The Team SkyePoint Difference
While we focus on Cybersecurity SkyePoint knows that we are not experts in every aspect of the Cyber landscape. To ensure mission success for our customers SkyePoint has a strong Partner network that can deliver the comprehensive cybersecurity capabilities our customers require.
- PPS Infotech is a small CMMI Service Level 3 company providing ICAM solutions to Federal Student Aid (FSA)
- MBL Technologies is a FedRAMP accredited 3PAO that provides Privacy Experts to support SAOP efforts in providing PTA’s, PIA’s and SORNs
- Dark Wolf Solutions provides an award-winning penetration testing capability that has been used to support the United States Air Force (USAF)
- ICF provides Cyber Range capabilities for the US Army
- CGI has been awarded DHS CDM Defend Groups C and F for their catalog of CDM capabilities and Services.
- Knight Federal provides RMF C&A and IV&V services for the DoD


Team SkyePoint Solution Elements
- Who is accessing the data? Team SkyePoint designs, implements, and integrates ICAM capabilities to provide customers with the situational awareness of who is accessing data. Using Zero Trust (ZT) principles we provide the capabilities to automate account management, password management, account lockout and multi-factor authentication approaches that increase situational awareness and reduce the threat surface of unmanaged and unattended accounts.
- What systems and devices are storing and processing data? Team SkyePoint provides capabilities through systems like Axonius to identify assets passively and automatically in the environment and tools like Lumeta that provide real time situational awareness across cloud, virtual and IoT systems.
- What protections are in place to protect the data? Throughout the RMF process Team SkyePoint identifies and implements controls to protect data and the systems that process the data. From custom Data Loss Prevention rules to STIG’s developed to our customers specific system categories, Privacy requirements and Risk tolerance we provide holistic capabilities to apply the right protections at the right place and time.
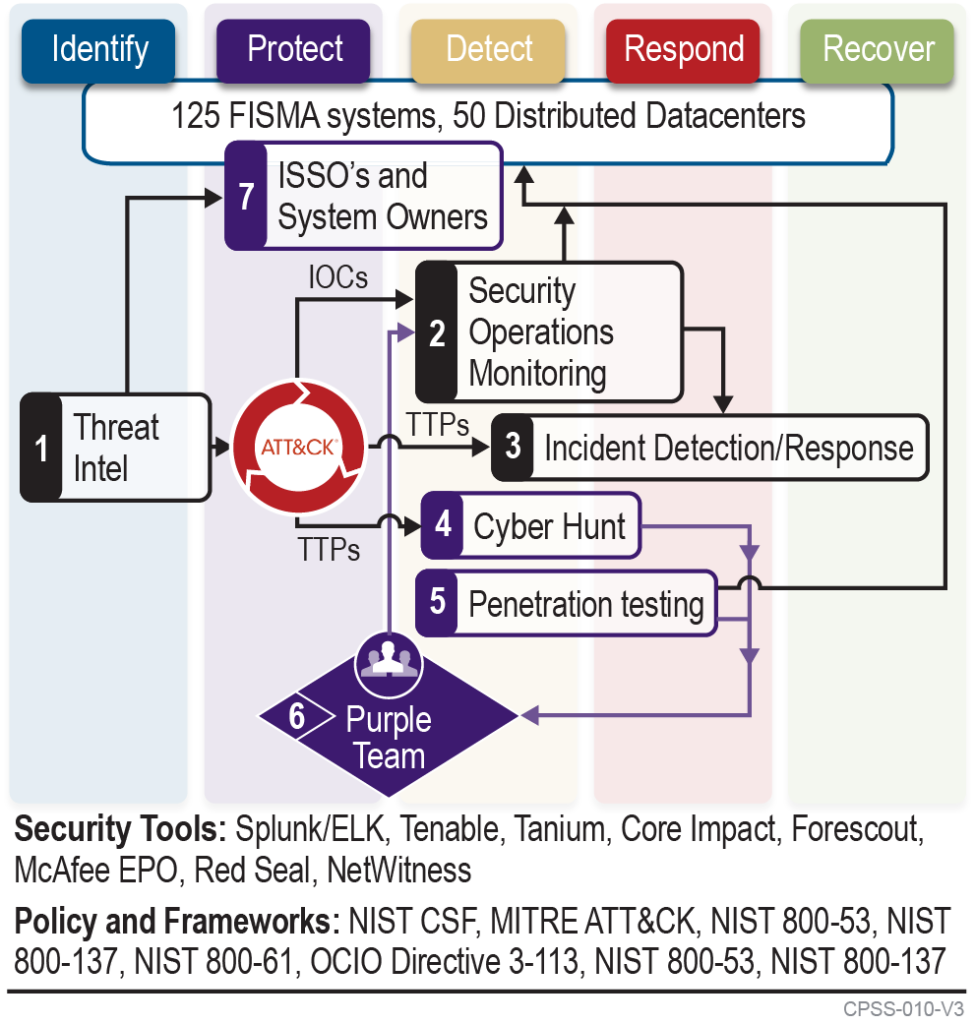
- How do we know those protections are effective? Our cybersecurity operations and continuous monitoring capabilities ensure our customers have the visibility and capabilities to evaluate controls based on known threat actors TTP’s and provide the ability to efficiently detect, respond and recover from active cyber events. Our Purple Team approach combines Threat Intel, Cyber Hunt, Penetration testing and Cyber Operations with System Owners and Administrators to rapidly plan, evaluate and remediate missing or ineffective protection, detection and response capabilities.

Benefits of a Trusted Team of IT Partners
- Reductions to the threat landscape while increasing situational awareness leads to increased compliance with federal mandates.
- The continuous monitoring and rapid enhancement of security controls through our Purple Team Approach
- Enhanced protections for PII and sensitive personal information
- Full service, full scope cybersecurity capabilities from a cohort of cybersecurity professionals
“SkyePoint Decisions has been consistently proactive in our relationship.
They reliably and professionally deliver innovative services.
Their understanding of critically needed technologies has made SkyePoint Decisions
a simple choice when considering companies with whom to partner.“
– Department of State Senior Manager